SRDS
1997
IEEE
13 years 8 months ago
1997
IEEE
This paper describes a fault detection mechanism that uses the error codes returned by the stream sockets to locate process failures. Since these errors are generated automaticall...
ICMI
2000
Springer
13 years 8 months ago
2000
Springer
Inferring users' actions and intentions forms an integral part of design and development of any human-computer interface. The presence of noisy and at times ambiguous sensory ...
GLOBECOM
2009
IEEE
13 years 8 months ago
2009
IEEE
This paper introduces a new framework of the multiple-input multiple-output (MIMO) detection in iterative receivers. Unlike the conventional methods processing with symbol lattice,...
ICC
2007
IEEE
13 years 8 months ago
2007
IEEE
In this paper, we consider energy-efficient routing for detection in wireless sensor networks (WSNs). Energyefficient routing for WSNs has been intensely studied recently, but rout...
WWIC
2010
Springer
13 years 8 months ago
2010
Springer
Abstract. In this paper we present and evaluate anomaly-based intrusion detection algorithms for detecting physical layer jamming attacks in wireless networks, by seeking changes i...
Publication
While objects of our focus of attention (“where we are looking at”) and accompanying affective responses to those objects is part of our daily experience, little research exis...
CCS
2007
ACM
13 years 8 months ago
2007
ACM
Remotely-launched software exploits are a common way for attackers to intrude into vulnerable computer systems. As detection techniques improve, remote exploitation techniques are...
HICSS
1994
IEEE
13 years 8 months ago
1994
IEEE
A method is described for identification and classification of proteins encoded in large DNA sequences. Previously, an automated system was introduced for the general detection of...
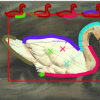
ECCV
2010
Springer
13 years 8 months ago
2010
Springer
Abstract. We propose a method for object category localization by partially matching edge contours to a single shape prototype of the category. Previous work in this area either re...
MIDDLEWARE
2009
Springer
13 years 9 months ago
2009
Springer
Today’s distributed systems need runtime error detection to catch errors arising from software bugs, hardware errors, or unexpected operating conditions. A prominent class of err...