67 search results - page 12 / 14 » Anonymizing transaction databases for publication |
TODS
2010
13 years 4 months ago
2010
: © A survey of B-tree locking techniques Goetz Graefe HP Laboratories HPL-2010-9 storage systems, databases, B-tree, indexes, concurrency control, locking B-trees have been ubiqu...
IRI
2007
IEEE
14 years 11 days ago
2007
IEEE
Crime reporting needs to be possible 24/7. Although 911 and tip-lines are the most publicized reporting mechanisms, several other options exist, ranging from inperson reporting to...
ICDT
2009
ACM
14 years 6 months ago
2009
ACM
In this paper, we present a comprehensive theoretical analysis of the sampling technique for the association rule mining problem. Most of the previous works have concentrated only...
Publication
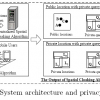
Existing location-based services provide specialized services to their customers based on the knowledge of their exact locations. With untrustworthy servers, location-based service...
DSS
2007
13 years 6 months ago
2007
chool of Business Research – FY 2007 Research Abstracts Dare to Share: Protecting Sensitive Knowledge with Data Sanitization Data sanitization is a process that is used to promot...