85 search results - page 17 / 17 » Time and Probability-Based Information Flow Analysis |
SP
2010
IEEE
13 years 3 months ago
2010
IEEE
A program is defined to be noninterferent if its outputs cannot be influenced by inputs at a higher security level than their own. Various researchers have demonstrated how this pr...
TPDS
2008
13 years 5 months ago
2008
Tracing IP packets back to their origins is an important step in defending the Internet against denial-of-service (DoS) attacks. Two kinds of IP traceback techniques have been prop...
Presentation
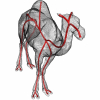
In this paper, we present a novel framework for computing centerlines for both 2D and 3D shape analysis. The framework works as follows: an object centerline point is selected auto...
Publication
In this paper, we present a novel framework for computing centerlines for both 2D and 3D shape analysis. The framework works as follows: an object centerline point is
selected aut...
GIS
2004
ACM
14 years 6 months ago
2004
ACM
Aerial video provides strong cues for automatic road extraction that are not available in static aerial images. Using stabilized (or geo-referenced) video data, capturing the dist...