10 search results - page 2 / 2 » Transient sensitivity computation for transistor level analy... |
SECON
2007
IEEE
13 years 11 months ago
2007
IEEE
— Wireless sensor networks are increasingly being employed for potentially hazardous and critical applications such as monitoring the gas concentration levels in a battle field....
ICDCS
2008
IEEE
13 years 11 months ago
2008
IEEE
The possibility of using purely text stream (keyboardenterable) as carrier of malware is under-researched and often underestimated. A text attack can happen at multiple levels, fr...
ISPA
2004
Springer
13 years 10 months ago
2004
Springer
Abstract. Current solutions for fault-tolerance in HPC systems focus on dealing with the result of a failure. However, most are unable to handle runtime system configuration change...
Publication
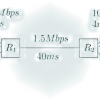
We propose Adaptive Multi-level ECN, a new TCP congestion scheme as an extension to Multi-level Explicit Congestion Notification (MECN). MECN algo- rithm allows network operators t...
TRIDENTCOM
2006
IEEE
13 years 11 months ago
2006
IEEE
—In this paper, we investigate the applicability of simulation and emulation for denial of service (DoS) attack experimentation. As a case study, we consider low-rate TCP-targete...