481 search results - page 23 / 97 » An Approach to Behavior Sharing in Federated Database System... |
211
click to vote
SIGMOD
2008
ACM
17 years 1 months ago
2008
ACM
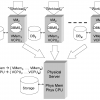
Virtual machine monitors are becoming popular tools for the deployment of database management systems and other enterprise software applications. In this paper, we consider a commo...
110
click to vote
DATE
2004
IEEE
15 years 5 months ago
2004
IEEE
In this paper we present an approach for analysis of systems of parallel, communicating processes for SoC design. We present a method to detect communications that synchronize the...
110
click to vote
APSCC
2006
IEEE
15 years 3 months ago
2006
IEEE
Detecting intrusions at host level is vital to protecting shared resources in grid, but traditional Host-based Intrusion Detecting System (HIDS) is not suitable for grid environme...
130
Voted
ISSADS
2005
Springer
15 years 7 months ago
2005
Springer
Workflow is the key technology for business process automation, while distributed workflow is the solution to deal with the decentralized nature of workflow applications and the pe...
SIGOPSE
2004
ACM
15 years 7 months ago
2004
ACM
This paper promotes accountability as a central design goal for dependable networked systems. We define three properties for accountable systems that extend beyond the basic secu...