10304 search results - page 1855 / 2061 » Computer science with the sciences: an emphasis in computati... |
124
Voted
COCO
2009
Springer
15 years 8 months ago
2009
Springer
—Consider the following Simultaneous Message Passing (SMP) model for computing a relation f ⊆ X ×Y ×Z. In this model Alice, on input x ∈ X and Bob, on input y ∈ Y, send o...
302
click to vote
Tutorial
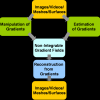
The last decade has seen a tremendous interest in gradient domain manipulation techniques for applications in vision and graphics including retinex, high dynamic range (HDR) tone m...
105
Voted
VIS
2004
IEEE
16 years 3 months ago
2004
IEEE
Determining the three-dimensional structure of distant astronomical objects is a challenging task, given that terrestrial observations provide only one viewpoint. For this task, b...
126
Voted
DAC
2007
ACM
16 years 2 months ago
2007
ACM
Randomness is inherent to biochemistry: at each instant, the sequence of reactions that fires is a matter of chance. Some biological systems exploit such randomness, choosing betw...
106
click to vote
WWW
2008
ACM
16 years 2 months ago
2008
ACM
Despite general awareness of the importance of keeping one's system secure, and widespread availability of consumer security technologies, actual investment in security remai...