205 search results - page 27 / 41 » Detecting algorithmically generated malicious domain names |
128
click to vote
INFOSCALE
2006
ACM
15 years 8 months ago
2006
ACM
Millions of Internet users are using large-scale peerto-peer (P2P) networks to share content files today. Many other mission-critical applications, such as Internet telephony and...
127
click to vote
IV
2009
IEEE
15 years 9 months ago
2009
IEEE
Most methods for generating Euler diagrams describe the detection of the general structure of the final draw as the first and most important step. This information is often depi...
131
Voted
ICMLA
2008
15 years 4 months ago
2008
Laser wakefield particle accelerators have shown the potential to generate electric fields thousands of times higher than those of conventional accelerators. The resulting extreme...
292
click to vote
Lecture Notes
The lecture notes cover the following topics,
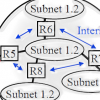
Fundamentals (OSI Reference Model, Coding, Ethernet), Data Link Control (Flow Control, Error Control, HDLC, PPP), Internet Protocol ...
141
click to vote
CVPR
2007
IEEE
16 years 4 months ago
2007
IEEE
This paper presents reliable techniques for detecting, tracking, and storing keyframes of people in surveillance video. The first component of our system is a novel face detector ...