212 search results - page 22 / 43 » Further analysis of the Internet key exchange protocol |
119
click to vote
IMC
2006
ACM
15 years 8 months ago
2006
ACM
A key step in the semantic analysis of network traffic is to parse the traffic stream according to the high-level protocols it contains. This process transforms raw bytes into s...
268
click to vote
Publication
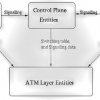
Asynchronous transfer mode (ATM) networks must define multicast capabilities in order to efficiently support numerous applications, such as video conferencing and distributed appli...
108
click to vote
ICIAR
2005
Springer
15 years 7 months ago
2005
Springer
There has been many hidden communication techniques proposed in the last few years. The focus was given to steganography to build such techniques. Utilizing stego-key(s) to hide se...
107
click to vote
CN
2007
15 years 1 months ago
2007
Soft-state is a well established approach to designing robust network protocols and applications. However it is unclear how to apply soft-state approach to protocols that must mai...
NETWORKING
2010
15 years 3 months ago
2010
We carry out a longitudinal study of evolution of small-time scaling behavior of Internet traffic on the MAWI dataset spanning 8 years. MAWI dataset contains a number of anomalies ...