364 search results - page 43 / 73 » Monitoring, Analyzing, and Controlling Internet-scale System... |
106
click to vote
MM
2010
ACM
15 years 1 days ago
2010
ACM
Automatic and real-time identification of unusual incidents is important for event detection and alarm systems. In today's camera surveillance solutions video streams are dis...
179
click to vote
SIGMOD
2008
ACM
16 years 11 months ago
2008
ACM
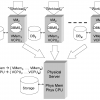
Virtual machine monitors are becoming popular tools for the deployment of database management systems and other enterprise software applications. In this paper, we consider a commo...
SIGCSE
2004
ACM
15 years 5 months ago
2004
ACM
This paper presents an innovative multiagent system to support cooperative learning among students both in the real classrooms and in distance education. The system, called I-MIND...
EUROSYS
2009
ACM
15 years 9 months ago
2009
ACM
Some web sites provide interactive extensions using browser scripts, often without inspecting the scripts to verify that they are benign and bug-free. Others handle users’ conď¬...
SIGCOMM
2010
ACM
15 years 1 days ago
2010
ACM
Privacy--the protection of information from unauthorized disclosure--is increasingly scarce on the Internet, and yet increasingly important as every user becomes both a content co...