770 search results - page 109 / 154 » Privacy Preserving Joins |
127
click to vote
ESORICS
2011
Springer
13 years 11 months ago
2011
Springer
Program authorship attribution—identifying a programmer based on stylistic characteristics of code—has practical implications for detecting software theft, digital forensics, a...
164
click to vote
ICDE
2012
IEEE
13 years 2 months ago
2012
IEEE
—We demonstrate DPCube, a component in our Health Information DE-identification (HIDE) framework, for releasing differentially private data cubes (or multi-dimensional histogram...
150
click to vote
Publication
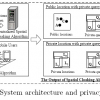
Existing location-based services provide specialized services to their customers based on the knowledge of their exact locations. With untrustworthy servers, location-based service...
105
click to vote
CCS
2005
ACM
15 years 5 months ago
2005
ACM
Policy enforcement is an integral part of many applications. Policies are often used to control access to sensitive information. Current policy specification languages give users ...
SP
2000
IEEE
15 years 4 months ago
2000
IEEE
In this paper, we describe a novel approach to scalable group re-keying for secure multicast. Our approach, which we call Kronos, is based upon the idea of periodic group re-keyin...