1335 search results - page 35 / 267 » Privacy in Database Publishing |
143
click to vote
SACMAT
2006
ACM
15 years 8 months ago
2006
ACM
In this paper we have addressed confidentiality and privacy for video surveillance databases. First we discussed our overall approach for suspicious event detection. Next we discu...
126
click to vote
IAJIT
2010
15 years 14 days ago
2010
: Privacy is one of the most important properties of an information system must satisfy, in which systems the need to share information among different, not trusted entities, the p...
128
click to vote
IEEEIAS
2007
IEEE
15 years 8 months ago
2007
IEEE
: Achieving privacy preservation in a data-sharing computing environment is becoming a challenging problem. Some organisations may have published privacy policies, which promise pr...
204
click to vote
Publication
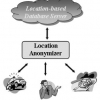
The wide spread of location-based services results in a strong market for location-detection devices (e.g., GPS-like devices, RFIDs, handheld devices, and cellular phones). Example...
136
click to vote
WPES
2003
ACM
15 years 7 months ago
2003
ACM
Traditionally, application software developers carry out their tests on their own local development databases. However, such local databases usually have only a small number of sa...