650 search results - page 46 / 130 » Privacy in Non-private Environments |
SP
2002
IEEE
14 years 9 months ago
2002
IEEE
The goal of the speech segments extraction process is to separate acoustic events of interest (the speech segment to be recognised) in a continuously recorded signal from other par...
CSREASAM
2009
14 years 7 months ago
2009
- Security is a primary concern in group communication, and secure authentication is essential to establishing a secure group communication. Most conventional authentications consi...
132
click to vote
ISSE
2011
14 years 4 months ago
2011
Application developers utilizing event-based middleware have sought to leverage domain-specific modeling for the advantages of intuitive specification, code synthesis, and suppo...
128
click to vote
Publication
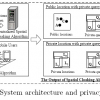
Existing location-based services provide specialized services to their customers based on the knowledge of their exact locations. With untrustworthy servers, location-based service...
CCS
2005
ACM
15 years 3 months ago
2005
ACM
Policy enforcement is an integral part of many applications. Policies are often used to control access to sensitive information. Current policy specification languages give users ...