164 search results - page 23 / 33 » Selecting and Improving System Call Models for Anomaly Detec... |
RIVF
2007
15 years 1 months ago
2007
This paper illustrates the use of acoustic modeling of spoken dialog systems. One major problem with using speech three different structures, including syllables, fillers and recog...
CVPR
2007
IEEE
16 years 1 months ago
2007
IEEE
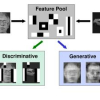
A major shortcoming of discriminative recognition and detection methods is their noise sensitivity, both during training and recognition. This may lead to very sensitive and britt...
CONEXT
2010
ACM
14 years 9 months ago
2010
ACM
Traditional DSL troubleshooting solutions are reactive, relying mainly on customers to report problems, and tend to be labor-intensive, time consuming, prone to incorrect resoluti...
106
Voted
GLOBECOM
2010
IEEE
14 years 9 months ago
2010
IEEE
Primary user emulation attack (PUEA) is a denial of service (DoS) attack unique to dynamic spectrum access (DSA) networks. While there have been studies in the literature to detect...
108
click to vote
CORR
2008
Springer
14 years 11 months ago
2008
Springer
The Voice over Internet Protocol (VoIP) is becoming a more available and popular way of communicating for Internet users. This also applies to Peer-to-Peer (P2P) systems and mergi...