110 search results - page 7 / 22 » Turning Teenagers into Stores |
102
click to vote
ACSAC
2007
IEEE
15 years 6 months ago
2007
IEEE
This paper describes the design and development of a software system to support law enforcement in investigating and prosecuting email based crimes. It focuses on phishing scams w...
EOR
2007
14 years 11 months ago
2007
Web sites allow the collection of vast amounts of navigational data – clickstreams of user traversals through the site. These massive data stores offer the tantalizing possibil...
CAD
2005
Springer
14 years 11 months ago
2005
Springer
Feature modeling systems usually employ a boundary representation (b-rep) to store the shape information on a product. It has, however, been shown that a b-rep has a number of sho...
105
click to vote
GVD
2009
14 years 9 months ago
2009
Over the last years the means to collect personal data implicitly or explicitly over the Web and by various kinds of sensors and to combine data for profiling individuals has dram...
173
click to vote
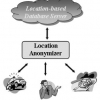
Publication
The wide spread of location-based services results in a strong market for location-detection devices (e.g., GPS-like devices, RFIDs, handheld devices, and cellular phones). Example...