922 search results - page 84 / 185 » Fairness, Resources, and Separation |
79
Voted
SAC
2002
ACM
14 years 10 months ago
2002
ACM
We describe a resource discovery and communication system designed for security and privacy. All objects in the system, e.g., appliances, wearable gadgets, software agents, and us...
DAIS
2009
14 years 11 months ago
2009
In future smart homes functionality will be provided to the inhabitants by software services decoupled from the underlying hardware devices. While this will enhance flexibility and...
HICSS
2010
IEEE
15 years 3 months ago
2010
IEEE
Recent advances in virtualization technologies have sparked a renewed interest in the use of kernel and process virtualization as a security mechanism to enforce resource isolatio...
137
click to vote
Publication
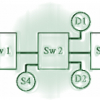
The OSU scheme is a rate-based congestion avoidance scheme for ATM networks using explicit rate indication. This work was one of the first attempts to define explicit rate switch m...
WCNC
2008
IEEE
15 years 4 months ago
2008
IEEE
— We consider the problem of centralized routing and scheduling for IEEE 802.16 mesh networks so as to provide Quality of Service (QoS) to individual real and interactive data ap...