1730 search results - page 247 / 346 » Shimura Curve Computations |
106
Voted
TC
2008
15 years 22 days ago
2008
Cryptanalysis of ciphers usually involves massive computations. The security parameters of cryptographic algorithms are commonly chosen so that attacks are infeasible with availabl...
127
click to vote
WSCG
2004
15 years 2 months ago
2004
Image registrations have been a subject of extensive study over the last decade. They appear in numerous applications including Computer Vision, Pattern Recognition, Medical Image...
385
click to vote
Presentation
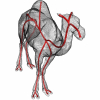
In this paper, we present a novel framework for computing centerlines for both 2D and 3D shape analysis. The framework works as follows: an object centerline point is selected auto...
130
click to vote
VIS
2003
IEEE
16 years 2 months ago
2003
IEEE
This paper presents a signed distance transform algorithm using graphics hardware, which computes the scalar valued function of the Euclidean distance to a given manifold of co-di...
120
click to vote
ICTAI
2008
IEEE
15 years 7 months ago
2008
IEEE
—The dynamics of many systems are described by ordinary differential equations (ODE). Solving ODEs with standard methods (i.e. numerical integration) needs a high amount of compu...